Azure is a popular cloud service provider owned and managed by Microsoft, it offers Platform and Infrastructure as a service for developers and software teams to build, test, manage, and deploy applications.
GitHub Actions is a powerful tool that allows developers to automate their workflows and improve productivity. GitHub Actions and Azure are two powerful tools that can greatly benefit developer teams. By connecting GitHub Actions to Azure, developer teams can automate their workflows and improve their productivity.
In this article, we will discuss how to connect GitHub Actions to Azure securely and provide some shortcuts that the GitHub guides don't show.
Benefits of integrating Azure with GitHub Actions
Find out the benefits of integrating the two CI/CD tools:
Workflow automation
One of the key benefits of GitHub Actions is the ability to automate workflows. Developer teams can create custom workflows that automate tasks such as building, testing, and deploying applications. These workflows can be triggered automatically based on specific events, such as code changes, pull requests, or releases.
By automating workflows, developer teams can save time and reduce errors. Manual tasks, such as building and deploying applications, can be time-consuming and error-prone. Automating these tasks with GitHub Actions can improve the speed and accuracy of the development process.
Integration with Azure
By integrating with Azure, developer teams can streamline their development process and improve their efficiency. They can take advantage of the many tools and services offered by Azure, without having to manage their own infrastructure. Get up to speed with the build process through repository monitoring for commits, or merges.
Improved Security
Another important benefit of connecting GitHub Actions to Azure that cannot be overlooked is improved security. GitHub Actions and Azure both provide a variety of security features that can help protect the application and data layer.
For example, GitHub Actions provides the ability to encrypt and store secrets securely. This helps to prevent unauthorized access to sensitive information, such as passwords and API keys.
Azure provides a variety of security features, such as network security groups, firewalls, and identity and access management. These features can help protect applications and data from external threats.
By using both GitHub Actions and Azure, developer teams can improve the security of their applications and data. They can take advantage of the many security features offered by these tools to help protect against unauthorized access and other security threats.
Managing Collaborations
GitHub Actions and Azure also provide powerful collaboration features that can benefit developer teams. By using these tools, developer teams can collaborate more effectively and efficiently.
For example, GitHub Actions provides the ability to create and share custom workflows with other team members. This can help to ensure that everyone is using the same processes and tools, which can improve the consistency and quality of the development process.
Azure provides a variety of collaboration features, such as role-based access control and team management. These features can help to ensure that team members have the appropriate access and permissions to perform their tasks.
By using both GitHub Actions and Azure, developer teams can collaborate more effectively and efficiently. They can take advantage of the many collaboration features offered by these tools to help ensure that everyone is working together effectively.
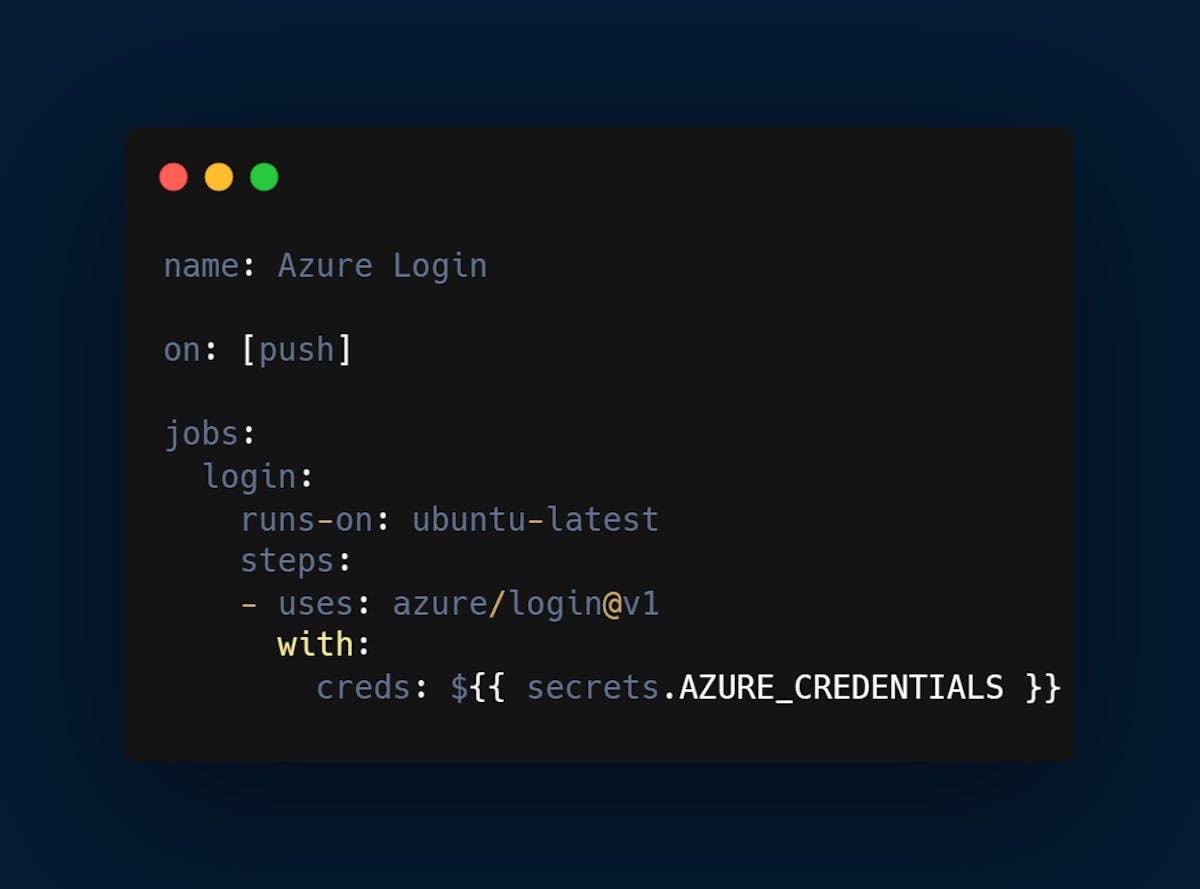
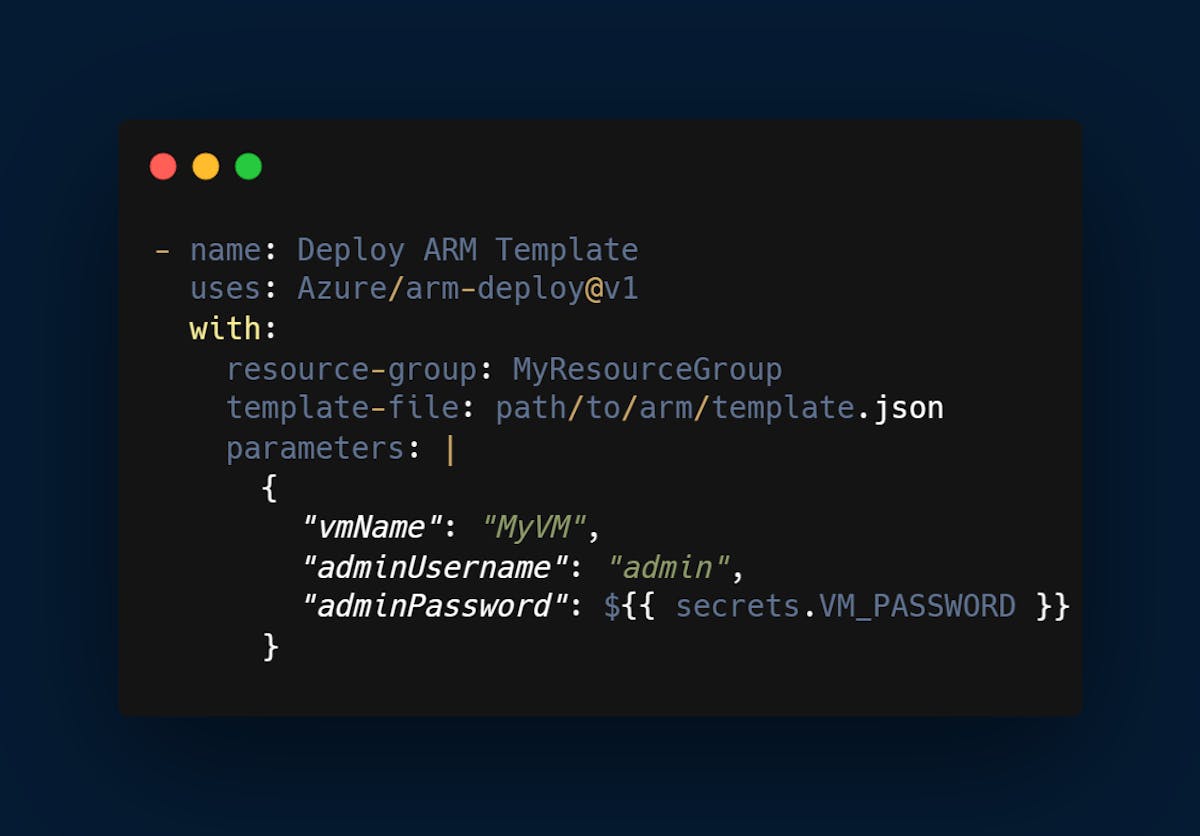
Setting Up Azure-GitHub Actions Integration
Follow the below steps to integrate the two:
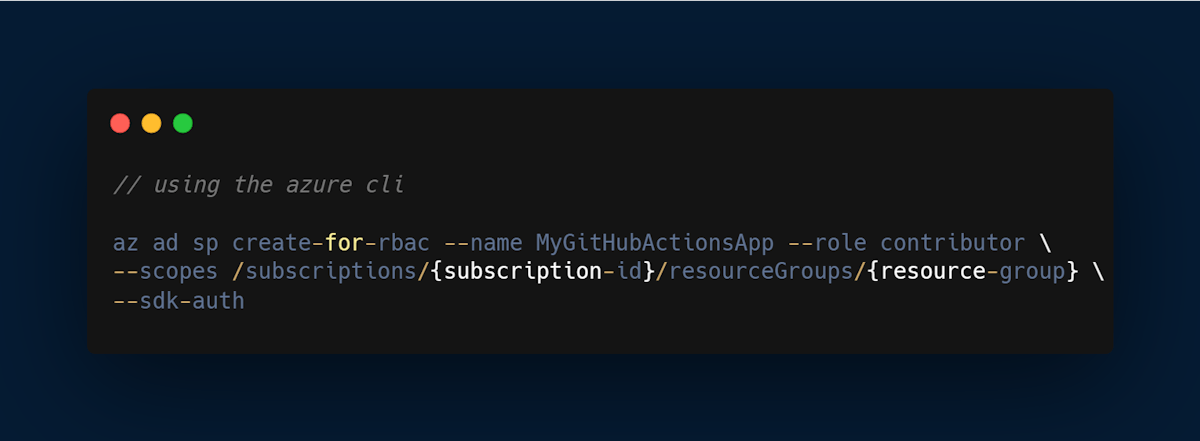
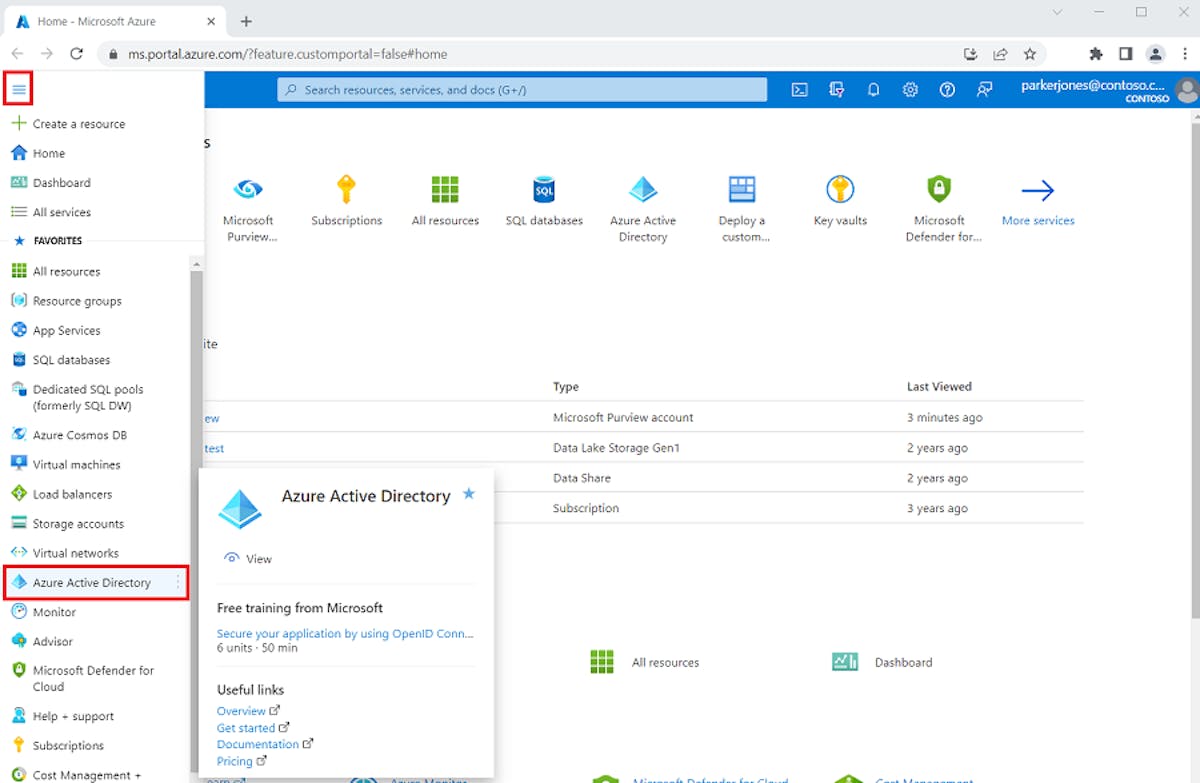
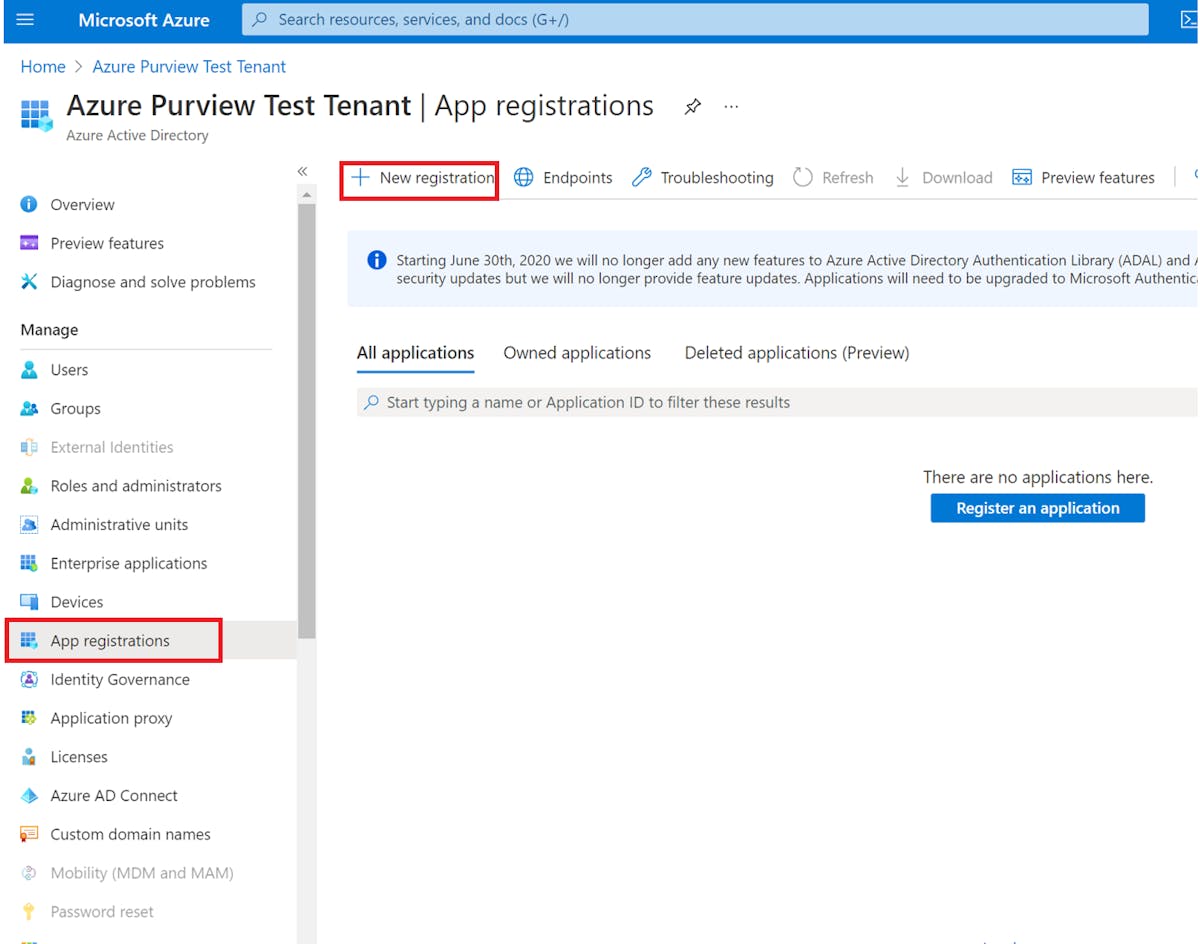
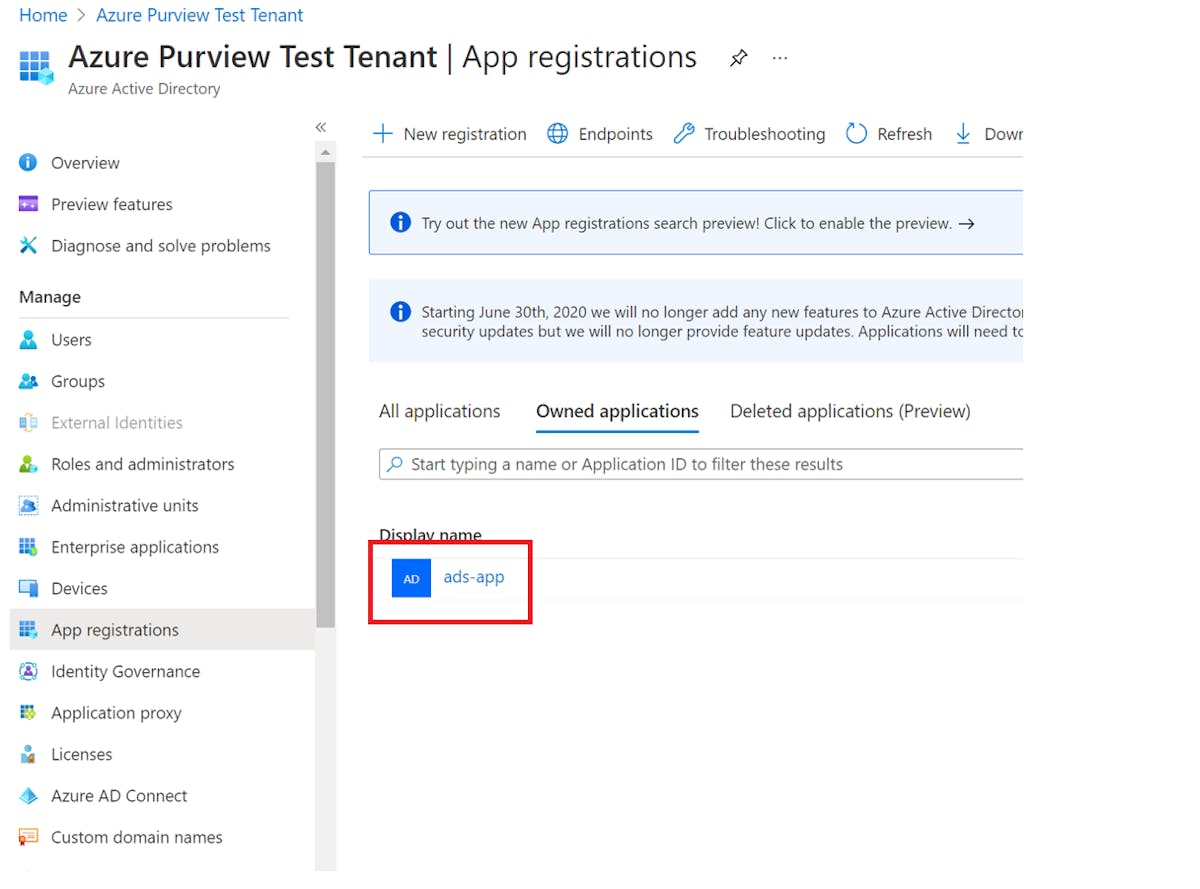
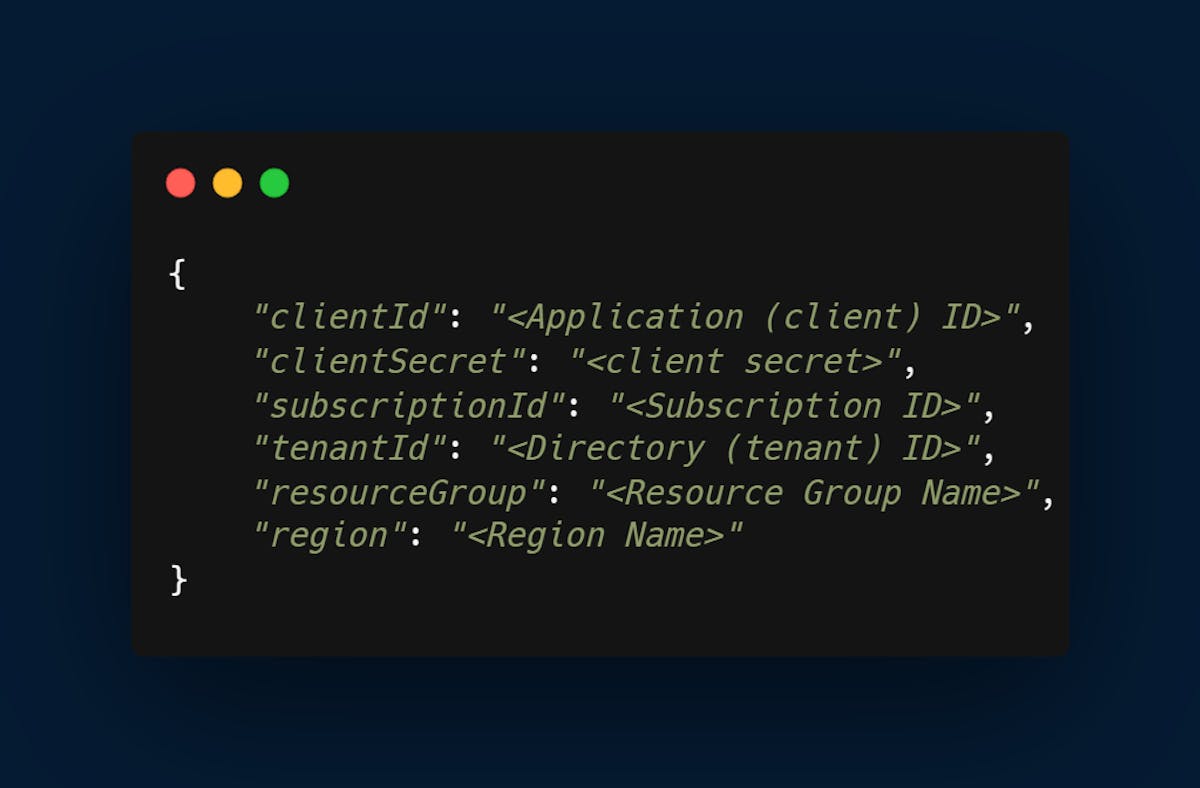
Step 1: Create an Azure Service Principal
Before you can connect GitHub Actions to Azure, you need to create an Azure Service Principal. The Service Principal is a security principal that provides access to Azure resources. You can create a service principal with the Azure CLI (see the image attached below), Azure Powershell, or on the Azure portal. For the article, I’ll be using the Azure portal, the service principal created will authenticate and authorize GitHub Actions to access Azure resources.